Build Secure Financial Applications on Blockchain
Build with modular protocols, developer-first tools, and open standards.
Learn More
Why Build on the Verified Network
Digital financial instruments built for modern investors, easy to access, secure, and always available.
Full Tech Stack
Complete development environment for security token applications

Secure by Design
Multi-party computation custody for maximum security

Compliant Token Standards
Enterprise-grade security token standards
Algorithmic Finance
ACTUS protocol for smart financial instruments
Two Powerful Ways to Build
A range of digital financial instruments built for modern investors, easy to access, secure, and always available.
JavaScript SDK
- Full access to Verified Network
- For front end applications development
- JavaScript support
- Access to smart contracts for securities, payments, custody
REST API
- Software interfaces for order management systems
- Multi-language support
- Secure authentication
- Access to smart contract based liquidity pools for subscriptions and trading

Program Smart Financial Instruments with ACTUS
Use the Verified Protocol, a JavaScript module based on the ACTUS standard, to issue tokenized securities that calculate payoffs and automate lifecycle events.
Supported Token Standards
Developers and ISVs implementing security tokens in an ERC compatible standard such as ERC-20, ERC-1400 or ERC-3643 can enable their secondary trading on the Verified Network. However, non ERC-20 features in ERC-1400 and ERC-3643 has to be supported in their host applications. Security tokens issued on the Verified Network implement a version of the CMTA standard.
ERC-20
Standard fungible token
CMTA
Advanced security features
Verified Custody
The Verified Custody module lets any frontend application add secure self-custody for users using multi-party computation (MPC). Users can add co-signers who must approve the user’s request to retrieve the private key. Private keys are never exposed, and users need not back up their passphrases.
A ready-to-use version is also available as a Chrome extension and will soon be coming on WalletConnect for easy integration in applications.
Build Your Own Flow
Offered as a customizable JavaScript module for seamless integration.
Secure Key Retrieval
Implements multi-party computation (MPC) techniques for secure key access.
Keyless Recovery
Doesn't require users to back up private keys or passphrases.
Decentralized Hosting
Doesn't require a centralized host and uses the blockchain as its host
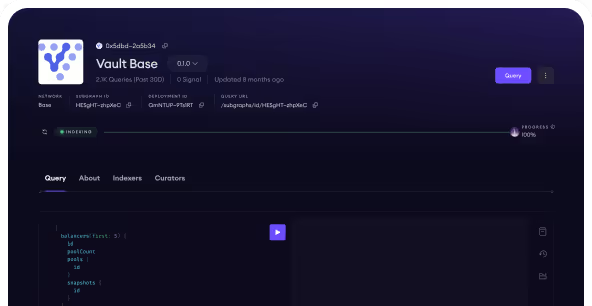
Query Securities Data with Subgraphs
Developers wishing to integrate securities product related data can use the Verified Subgraphs for querying using graphQL. All data schemas that do not have a personally identifiable wallet key as an identifier can be used to query generic data.
Wallet Base
Query user wallet specific data around securities and payments.

Vault Base
Query liquidity pool specific data for orders and settlements.
Are you interested to join the Verified Network?
Join the leading organizations that issue digital securities and service investors and issuers.
Contact UsAre you interested to join the Verified Network?
Join the leading organizations that issue digital securities and service investors and issuers.

Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
.svg)

